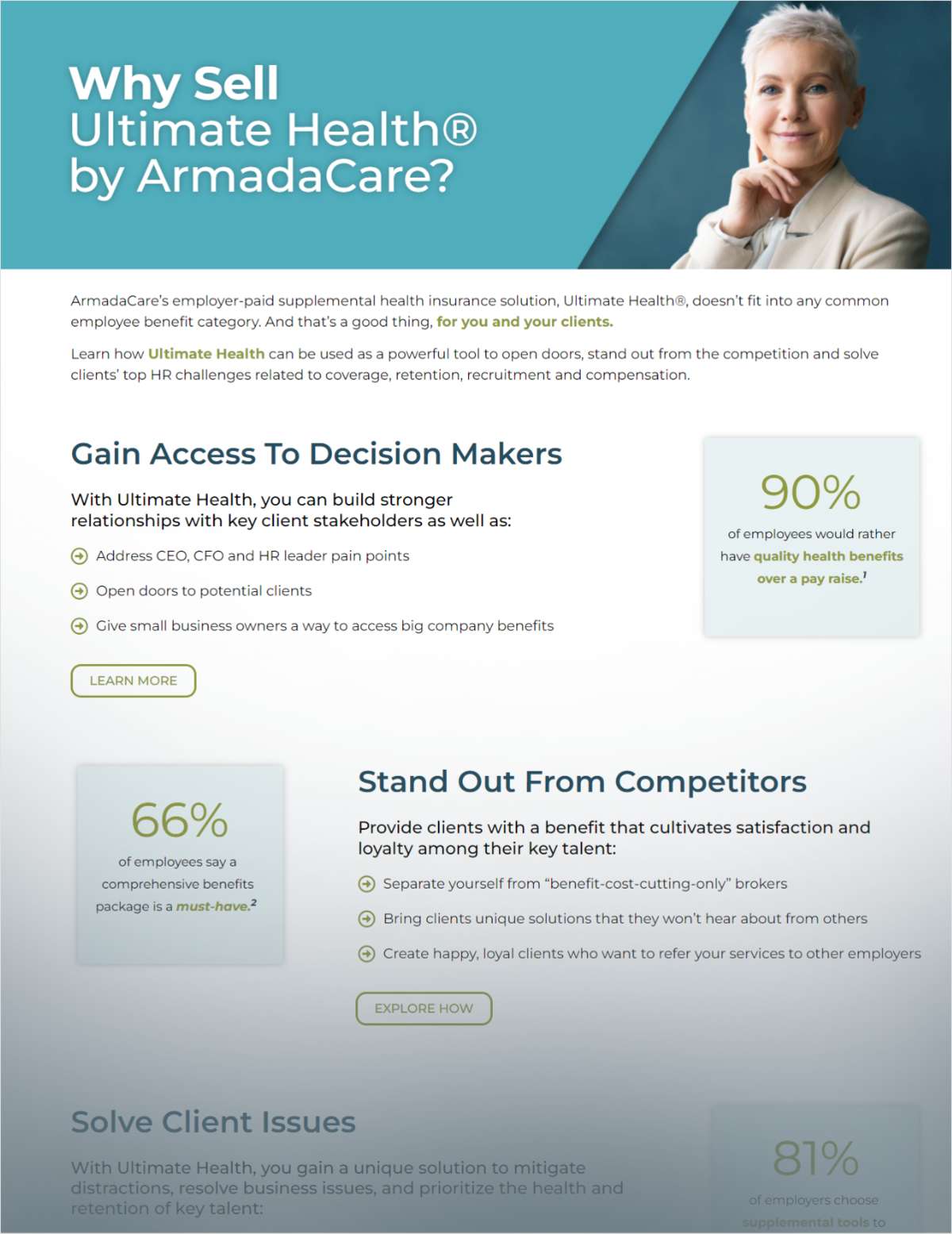
Employers who are subject toHIPAA must ensure they have the proper monitoring protocolsand policies in place to quickly and aptly tackle any violations.(Photo: Shutterstock)
Employers who are subject toHIPAA must ensure they have the proper monitoring protocolsand policies in place to quickly and aptly tackle any violations.(Photo: Shutterstock)
A recent case highlights how one medical providerappropriately managed its HIPAA compliance by consistentlyenforcing its policies and keeping tabs on who accessed protectedhealth information. While the case involves a provider, employerswith health plans subject to HIPAA can also learn some valuablelessons from this case.
|Background
Lankenau Medical Center (Lankenau) is an acute care hospitalthat is part of Main Line Health (MLH), a not-for-profit healthsystem. Gloria Terrell (Terrell) worked as an operating room (OR)secretary for Lankenau for more than 35 years. As an OR secretary,Terrell was responsible for the OR schedule, calling for patients,sending for blood and medications, patient billing and charts,office supplies, ordering uniforms and other related duties.
|In her capacity as OR secretary, Terrell had access to thehospital system used to store various forms of protected health information such as patientnames, dates of birth, social security numbers, phone numbers, andinsurance information. However, she did not have access to patientmedical charts. As in many health care organizations, employeeswere often also patients of Lankenau.
|On August 15, 2016, Terrell accessed a coworker's home phonenumber in the MLH system. Seven days later Terrell accessed itagain. Generally, employee phone numbers are kept in a list on aclipboard in the OR. However, the clipboard had been missing onboth occasions.
MLH Policies
As a medical provider, MLH is subject to the privacy regulationsunder the Health Insurance Portability and Accountability Act(HIPAA). In particular, MLH has a number of policies and processesdesigned to ensure the privacy of patient information andcompliance with HIPAA:
- Confidentiality Policy – requires employees tosafeguard various types of private and/or protected information.Employees have to sign a confidentiality statement that theemployee will only access patient/employee information “about whomI have business need to know.”
- Code of Conduct and Behaviors that Undermine a Cultureof Safety (“Code of Conduct”) – prohibits unauthorizeddisclosure, access, and/or release of confidential, ProtectedHealth Information (PHI) and prohibits unauthorized use of the MLHsystems.
- Annual HIPAA training and testing – employeesare required to complete annual HIPAA training and testing whichincludes explanations and examples of the HIPAA compliance rulessuch as:|
- PHI under the MLH policy includes “any information identifiableto a patient” such as name, address, email, etc.
- The patient must authorize disclosure unless it is needed fortreating the patient, patient payment, or health careoperations.
- Employees are instructed, and acknowledge, that they must“access only information you need to do your job” and “use theinformation to perform your job only”
To monitor for compliance, MLH implemented privacy monitoringtechnology. The technology monitored employee system usage foraccess to Personally Identifiable Information (“PII”) and/or PHI toidentify usage that is not based on legitimate businesspurposes.
|Employees who violate MLH policy are subject to a performancemanagement policy that includes disciplinary action up to andincluding termination. It was a violation of the policy to access“PHI outside the scope of job duties (to compare coworkerworkloads, learn about clinical operations)” and/or check “on acoworker, family member or neighbor.”
|Terrell's conduct and policy violations and the fallout
Terrell's access on August 15th was flagged by a technologymonitoring system. As a result, MLH launched an investigation andfound Terrell's second access that occurred seven days later.
|In her defense, Terrell claimed she believed that she had alegitimate business need. On both occasions, Terrell claimed shewanted to call the employee to be sure she was coming in to work onthat day. However, Terrell's supervisor testified that this was notpart of her regular duties and neither the supervisor nor thecoworker gave her permission to access the employee's home phonenumber in the MLH system.
|Because Terrell access to MLH's system was not permitted, MLHfound that Terrell had violated its policies. Given the seriousnessof her violations, even after 35 years, MLH terminated Terrell'semployment.
|Subsequently, Terrell filed an age discrimination claim arguing that thetermination was not because of her violations, but instead becauseof her age. Plaintiff claimed that the reason for her terminationwas really a “pretext” for age discrimination. To show pretext, theTerrell had to demonstrate that the hospital had actedinconsistently in the past and in favor of those who are notprotected by the Age Discrimination in Employment Act (i.e. underage 40). The court rejected this argument stating that Terrell hadprovided no evidence of her allegations of pretext.
|The court emphasized that the employer had several policies inplace that specifically and clearly prohibited Terrell's conduct.Additionally, the court found that the employer provided trainingand had consistently enforced these policies regardless of theemployee's age. Terrell's behavior violated HIPAA, MLH'sConfidentiality Policy, and its Code of Conduct and that was alegitimate reason for her termination. Moreover, termination wasthe contemplated consequence for the violation of each of these MLHpolicies.
|Takeaways for employers
This is a great example of what an employer should do! Employersthat are, or that have plans, subject to HIPAA should:
- Ensure you have HIPAA and disciplinary policies that are wellwritten, clear, and understandable
- Provide examples of prohibited conduct
- Enforce your policies consistently and across the board – don'tmake exceptions or vary your response to similar violations andmisconduct
- Ensure that employees are trained and tested on a regular basis– here, MLH trained and tested employees annually
- Monitor employee conduct and behavior for compliance – whetheryou implement technology system or manually monitor employees,staying on top of employee's conduct is essential
- Be sure that if you are a medical provider that provides careto your employees that they are included in the protections offeredby your policies
 Carrie Cherveny isthe senior vice president of strategic client solutions in HUB's RiskServices Division. She has 20 years of combined experience inemployee relations working on the management side providing humanresources, employment law, and employee benefits legalguidance.
Carrie Cherveny isthe senior vice president of strategic client solutions in HUB's RiskServices Division. She has 20 years of combined experience inemployee relations working on the management side providing humanresources, employment law, and employee benefits legalguidance.
Complete your profile to continue reading and get FREE access to BenefitsPRO, part of your ALM digital membership.
Your access to unlimited BenefitsPRO content isn’t changing.
Once you are an ALM digital member, you’ll receive:
- Critical BenefitsPRO information including cutting edge post-reform success strategies, access to educational webcasts and videos, resources from industry leaders, and informative Newsletters.
- Exclusive discounts on ALM, BenefitsPRO magazine and BenefitsPRO.com events
- Access to other award-winning ALM websites including ThinkAdvisor.com and Law.com
Already have an account? Sign In
© 2024 ALM Global, LLC, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more information visit Asset & Logo Licensing.