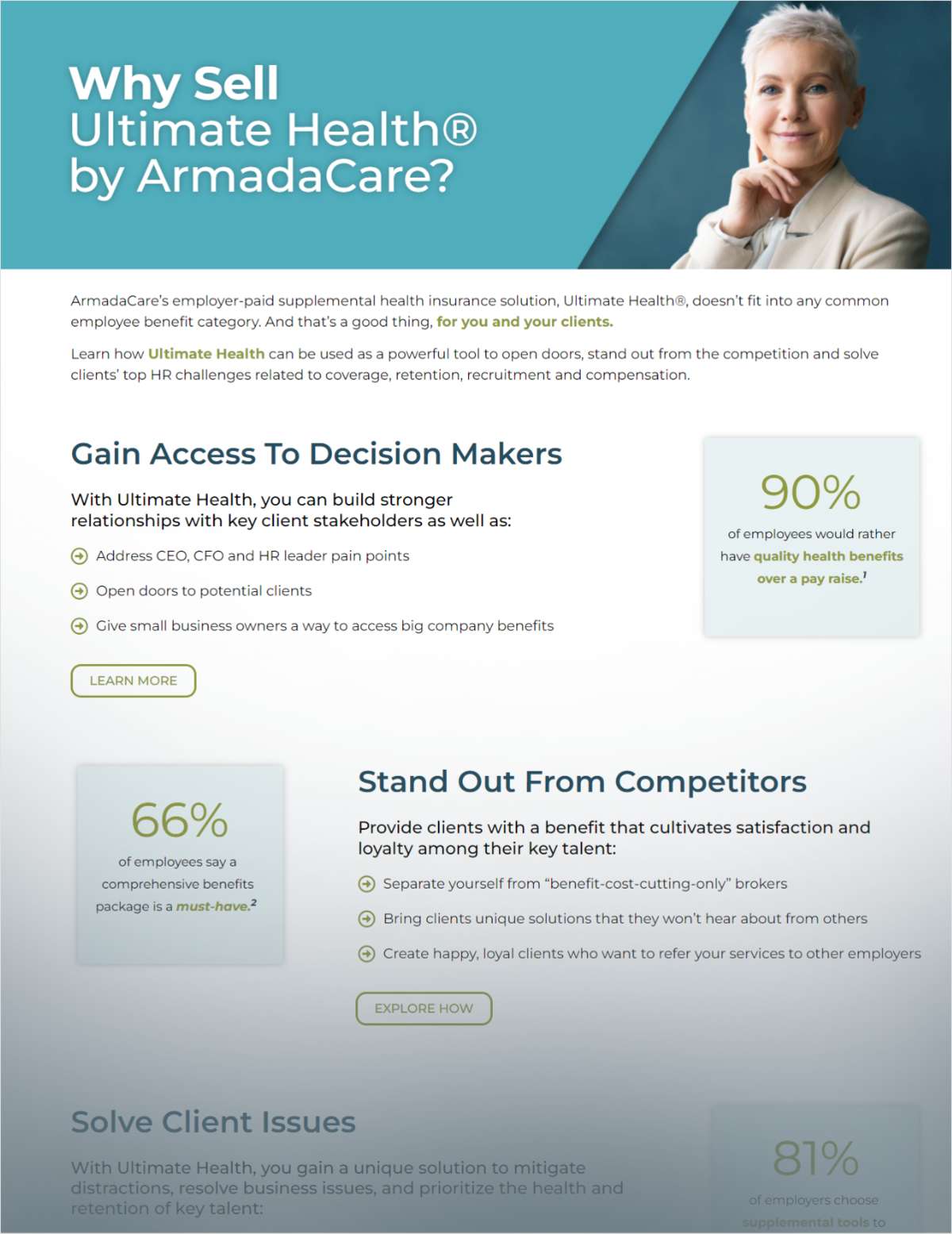
In today's increasingly digital world, the primary threats that aim todisrupt your business and the business of your client's can comefrom a variety of sources and malicious applications. Below are thefive biggest cyber threats I've identified from my work onRelativityOne that could impact your business along with how youcan protect yourself from each.
|1. Phishing
Phishing is arguably the most important threat vector to worryabout. Your people are already inside your perimeter, behind yourfirewall and have access to your resources and protected assets.This is why phishing attacks are the way most malware gets intoorganizations—download because an internal user clicked on a linkor attachment in a phishing email. Wombat Security has said that 76percent of businesses have been a victim of a phishing attackwithin the last year and SANS Institute reported that 95 percent ofall attacks on enterprise networks are the result of successfulspear phishing.
|Training on how to detect a phishing email remains the bestdefense but it isn't a one-and-done approach, training needs to berepeated multiple times per year, and it is recommended that youphish your own people at regular intervals to spot check andprovide constructive feedback. Verizon has reported that 30 percentof phishing messages get opened by targeted users and 12 percent ofthose users click the malicious attachment or link. Sophisticatedphishing attacks are designed to look real—that's why people arefooled into clicking with devastating results.
|2. Crypto-currency mining
Crypto currency mining malware has become a hot topic in 2018.Criminals have found the way to immediately profit from criminalactivity without having to sell information or extort themoney—just use up your resources to mine it. The top threecryptocurrencies, by market capitalization, are Bitcoin (BTC)trading at over $7,000 USD each, Ethereum (ETH) trading at almost$300 USD each, and Ripple (XRP) trading at $0.34 USD each. WhyRipple? Because it's being used as a real-time gross settlementsystem enabling near instant and direct transfer of money betweentwo parties.
|One might think that one of these would be the most mined cryptocurrencies, but in fact it is number 11 on the list—Monero (XMR)trading at just over $100 USD each. The reason is the computationpower required to mine for the coin and the value obtained vs. thework performed. A higher return on mining effort is available fromMonero than other cryptocurrencies. Malware is the delivery tool,often through phishing, to drop the payload of a Monero miner onvictim computers. Whether in the cloud or on-prem, once the minersoftware is loaded it begins to work on finding coins for theattacker and depositing them into their collection pools andwallets. The more of your computers they can infect, the bigger thepayday. It's a direct payout for the attackers who have to donothing further.
|The concerns are that you are losing resources that you can'tuse for the reason you purchased them—serving web pages, developingsoftware, etc.—enabling your business. Even more insidious is thatyou now have software under the control of attackers on yournetwork. They can add additional malware, like ransomware, Trojans,RATs, or anything they like really, at any time. The solution isthe same for any malware, a defense-in-depth strategy to find andeliminate threats at as many levels in your architecture aspossible. Firewalls at the perimeter all the way down to host-basedAV and EDR solution on the endpoint.
|3. Ransomware
Ransomware is malicious software (malware) that infects yourmachine and begins by quietly encrypting files. Once it has doneits work, it presents you with a ransom note that to see your filesagain, you're going to have to pay. The price is always in acryptocurrency, usually Bitcoin (BTC) per machine to decrypt yourfiles. The attackers are willing to decrypt a few files for free inmost cases, to prove they can, and have even taken to negotiatingwith companies who try to lower the extortion payment.
|Paying that ransom is the wrong move unless you have no otheroption available. You're directly funding the crime and thecriminals if you pay, which will only encourage them to continuedoing it. Further, you're now in the list of people who pay whenextorted, so you can almost guarantee to pay again in the future.The solution to ransomware is a well-defined and executed disasterrecovery/backup and restore program. You should be backing up yourassets at regular intervals and frequently testing restore andrecoverability. If you can restore your organization from backup,why pay a ransom?
|4. Nation state/APT actors
Nation state Actors, also known as advanced persistent threat(APT) actors, are a concern of larger organizations. Primarily thereasons a nation-state would target your organization are to stealintellectual property, influence political decisions, or to causedamage, physical or monetary. These are often the “unknownunknowns” of threats. There are things you know, things you knowyou don't know, and this other category: what you don't know thatyou don't know. These scare people more than anything else—andreally they shouldn't be at the very top of your list if you'redoing security the right way.
|Honestly, a persistent actor who goes after somethingrelentlessly will eventually get it. They're trying to do itquietly and covertly, but if that fails, a smash and grab will workjust as well. Implementing a security program with adefense-in-depth strategy is your best defense. Hunting teams haveuncovering unknown unknowns as part of their charter. No one can bethe “abnormality” on your network and be completely silent. It isyour diligence that will let you find these threats sooner,minimize losses, and may even help you avoid the lossaltogether.
|5. Insider threat
The final category in the top five cyber threats list is theinsider threat. These generically come in two flavors: theunintentional and the intentional. Most of your security policy andprogram focuses around prevention of unintentional losses from youremployees. It's the intentional criminal you have to hunt down. Whydo your employees become an intentional threat actor? Many do it tosteal property or information for personal gain or to benefitanother organization or country. Most of the reported cases ofinsider threat (>80%) to date have been done during workinghours, with the activity planned beforehand, and financial gain asthe motive. Revenge and having real financial difficulties have notshown to be a majority of the reasons in insider threat cases todate.
|This is the hardest type of attacker to find. It requiresforensic examination of your network and assets to uncover. Thereare many things you can do to lessen the impact of an insiderthreat. Physical security of employee devices can help mitigatelosses in cases of insider threat; a well-implemented assetmanagement solution can prevent lost or stolen devices from givingattackers valuable information. Connection to insecure networks,particularly unsecured wireless networks, is another preventativemeasure to help loss from unintentional insider threats. Your bestoverall protection is still a fully developed and implementedsecurity program. Remember, security isn't a product or somethingyou buy, it's what you do every day.
Darian Lewis is the Lead ThreatIntelligence Analyst in Relativity's security group, Calder7. Inhis role, Darian leads a team in charge of assessing and respondingto threats that could impact the security of Relativity's SaaSproduct, RelativityOne.
Complete your profile to continue reading and get FREE access to BenefitsPRO, part of your ALM digital membership.
Your access to unlimited BenefitsPRO content isn’t changing.
Once you are an ALM digital member, you’ll receive:
- Critical BenefitsPRO information including cutting edge post-reform success strategies, access to educational webcasts and videos, resources from industry leaders, and informative Newsletters.
- Exclusive discounts on ALM, BenefitsPRO magazine and BenefitsPRO.com events
- Access to other award-winning ALM websites including ThinkAdvisor.com and Law.com
Already have an account? Sign In
© 2024 ALM Global, LLC, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more information visit Asset & Logo Licensing.